What is the AWS Access Key?
AWS Access Key, part of AWS security credentials, is a unique identifier associated with an AWS Identity and Access Management (IAM) user or role. It is used in combination with a secret access key to sign programmatic requests to the AWS API. These requests can be made using the AWS Command Line Interface (CLI), AWS SDKs (Software Development Kits), or directly through the AWS APIs. Together, the access key ID and the secret access key authenticate the identity of the requester to AWS services, ensuring secure access to AWS resources.
Components of AWS Access Key
AWS Access key has to main component Access key and secret access key.
Access Key ID: This is the public part of the key, similar to a username. It identifies the AWS account and the IAM user or role making the request. It’s visible and shareable, used in combination with the secret access key to securely access AWS services.
Secret Access Key: This is the private part of the key, the same as a password. It’s used to sign requests to AWS programmatically. For security reasons, AWS only shows the secret access key once at the time of creation. You must keep it confidential to prevent unauthorized access to your AWS resources.
Why use the AWS Access Key?
AWS Access Keys provide a secure method for authenticating and authorizing programmatic requests to AWS services. They are essential for using the AWS CLI, SDKs, and direct API calls, allowing developers and system administrators to interact with AWS resources programmatically. This enables seamless integration of AWS services into application workflows, automation scripts, and infrastructure management tasks, ensuring secure and efficient operation of cloud-based environments.
Creating Access Key
To create an AWS Access Key you must log into your AWS Console and navigate to IAM. Then from “Access management” select “Users”. From there you will be able to see all the available users. Now select the username to which you want the access key to belong.
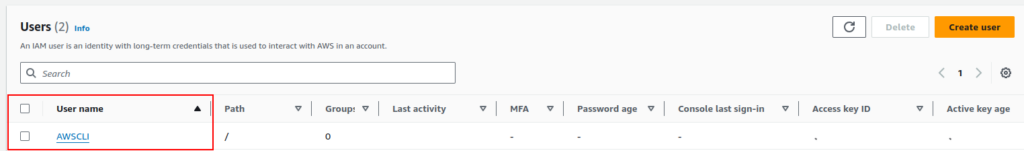
Remember the access key will get permission depending on the permission set on the user itself.
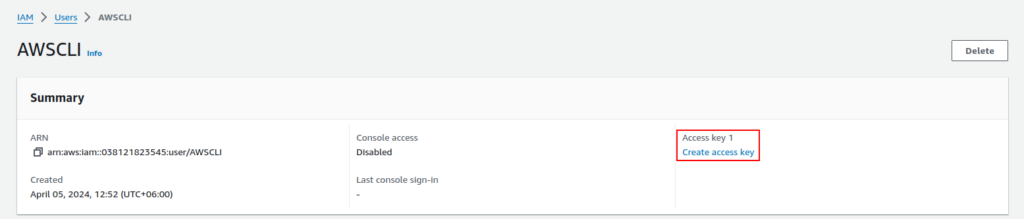
Now from the summary click on “Create access key”.
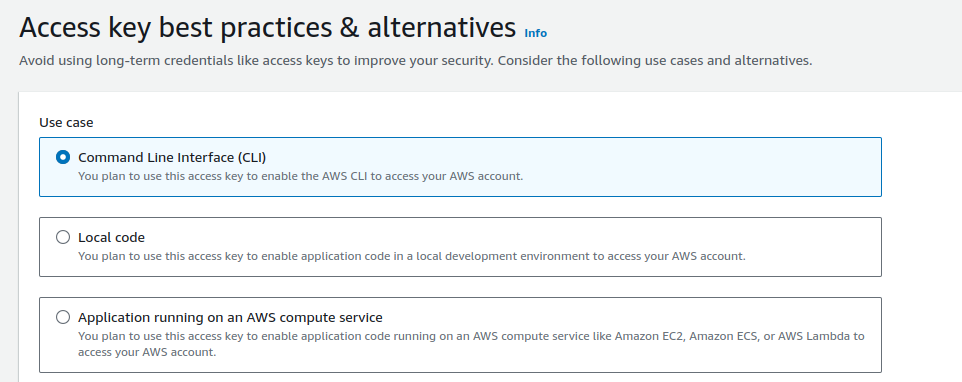
Select “Command Line Interface (CLI)” and click next. You can use other options if you are creating the access for different purposes.
Next, you can set a description tag and click on “Create access key”. This description tag is optional so you can skip it if you prefer.
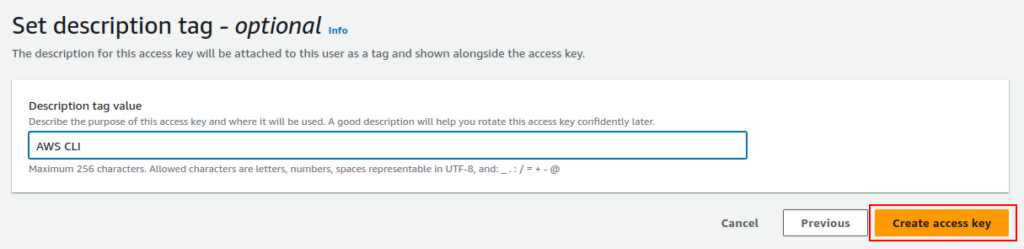
This will create the access key.
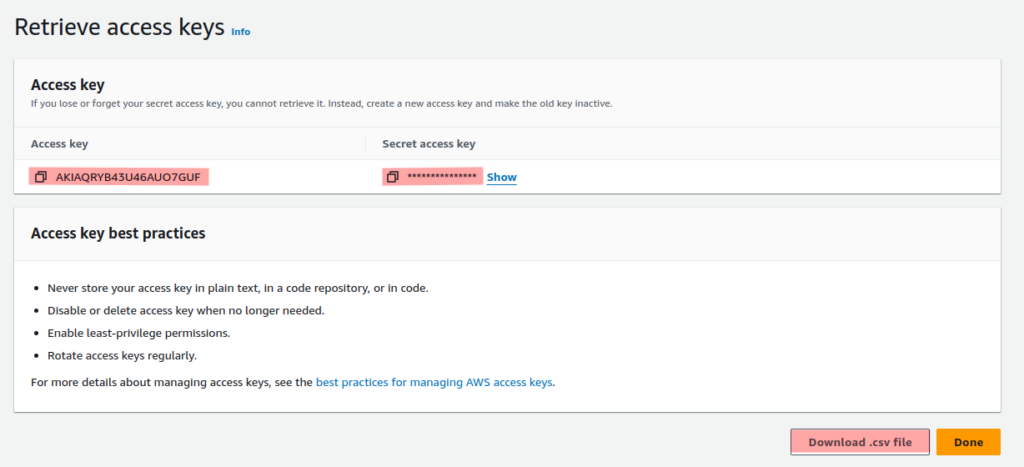
Here you can download the Access key and secret access key in a CSV file. Or directly copy and paste it from here. One thing to remember is that the secret access key can only be accessed once if you leave this page you won’t be able to access it.
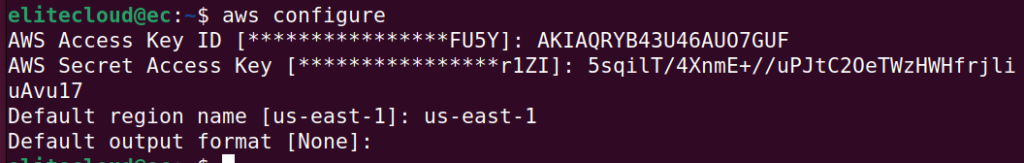
You can now use the command `aws configure` to configure the access key with AWS CLI.
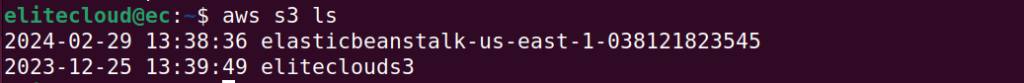
You can now perform all the actions from your AWS CLI depending on the permission belonging to the access keys.
Deactivating the Access Key
Once you are finished with your access key. It’s best practice to deactivate your access key to stop unauthorized access.
Navigate to the user and go to the “Security credentials” tab.
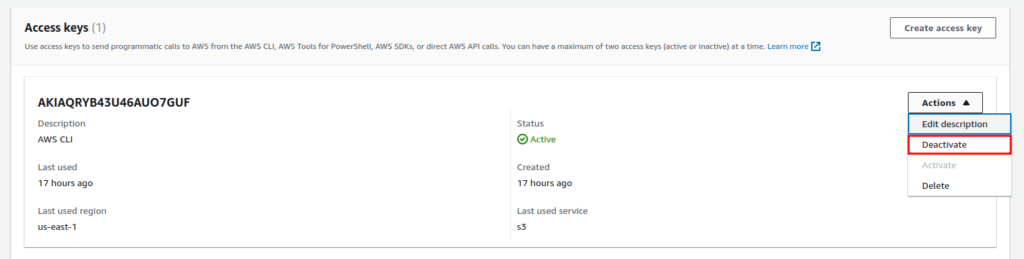
Scroll down to the “Access Keys” section, and from the “Actions” dropdown, select Deactivate.
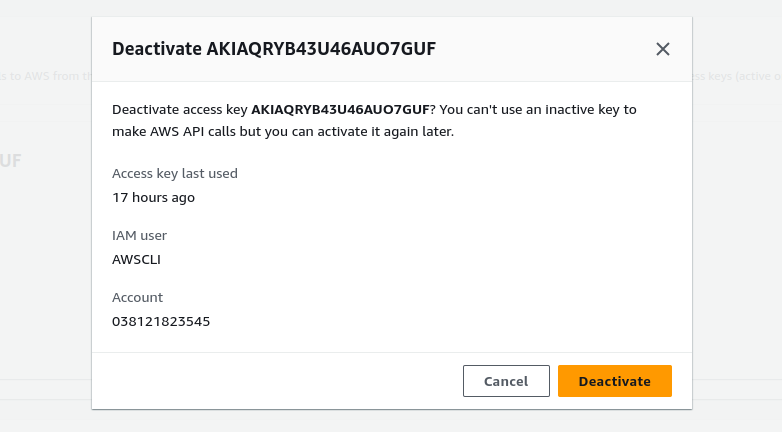
Next, follow the confirmation.
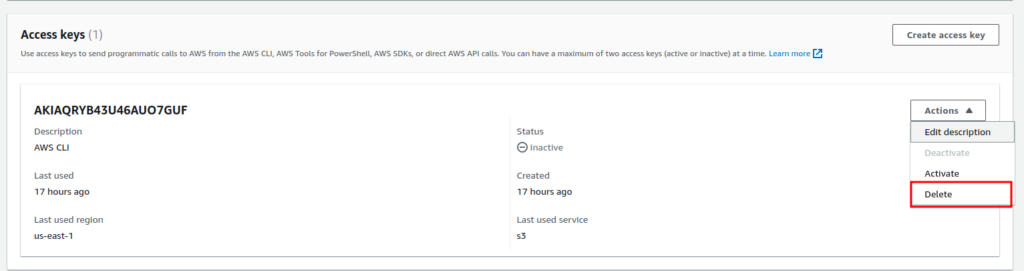
Your access key will be deactivated, and if you no longer need this access key you can go ahead and delete it same as deactivating.
🔑 Struggling to manage AWS Access Keys securely?
Elite Cloud provides expert guidance on creating, rotating, and securing AWS Access Keys, helping you avoid common pitfalls and enforce best practices across your environment.
👉 Book a session with the Elite Cloud team today and take control of your cloud credentials before they become a security risk!