In this hands-on tutorial, we will set up AWS Macie, upload sensitive data to Amazon S3, scan for risks, and analyze the findings. AWS Macie helps detect personally identifiable information (PII), financial data, and other sensitive content in cloud storage, providing security teams with actionable insights.
By the end of this tutorial, you will have practical experience with Macie’s scanning and classification capabilities.
Prerequisites
- An AWS account with permission to use Amazon S3 and AWS Macie.
- AWS Macie enabled in the AWS Management Console.
- At least one S3 bucket is available for testing.
Step 1: Enable AWS Macie
Before scanning for sensitive data, AWS Macie must be enabled.
Log in to the AWS Management Console. Navigate to AWS Macie (search for “Macie” in the AWS services search bar).
Then click on Get Started.
After that click Enable Macie.
Once enabled, Macie will begin scanning S3 buckets for security issues such as publicly accessible data or misconfigured permissions.
Step 2: Upload a File Containing Sensitive Data to Amazon S3
To test Macie, upload a file that contains fake sensitive information, such as credit card numbers and social security numbers.
1. Create a Test File
Open a text editor and create a file named test_data.txt. Add the following sample data:
Name: John Doe
Email: [email protected]
Credit Card: 4111-1111-1111-1111
SSN: 123-45-6789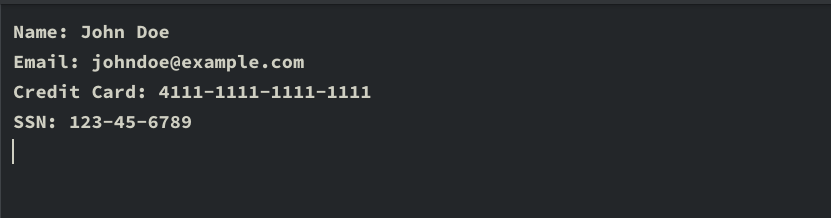
Save the file as test_data.txt.
2. Upload the File to S3
Go to Amazon S3 in the AWS Console. And select an existing S3 bucket or create a new bucket.
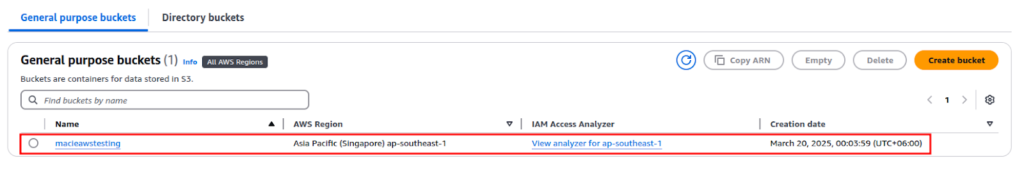
Now click Upload, then select test_data.txt.
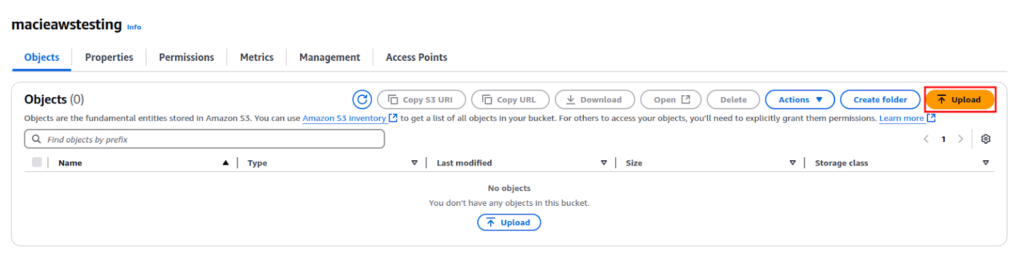
Again click Upload to store the file in S3.
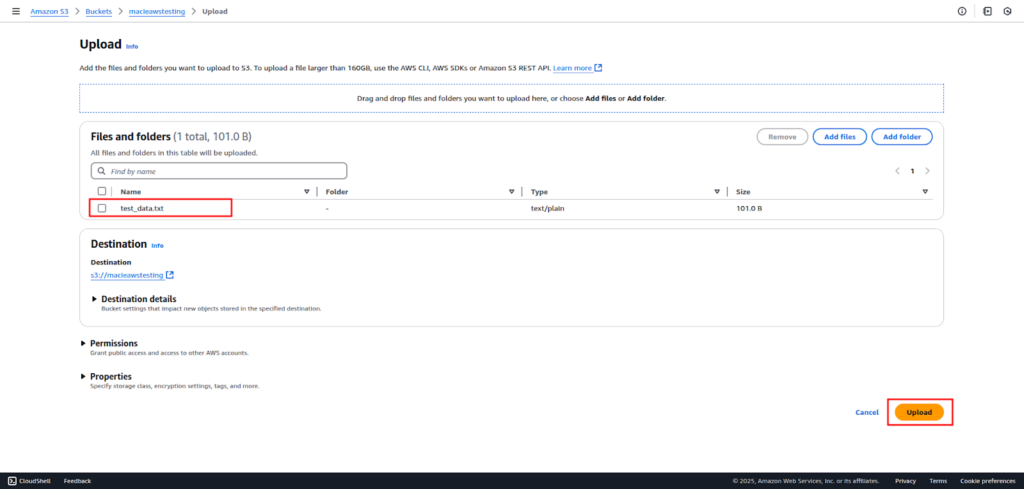
Step 3: Configure AWS Macie to Scan the S3 Bucket
Now, we will configure Macie to scan the bucket and identify the sensitive data.
Create a Macie Job for Data Discovery
In the AWS Console, go to Macie. And click Create Job to set instructions.
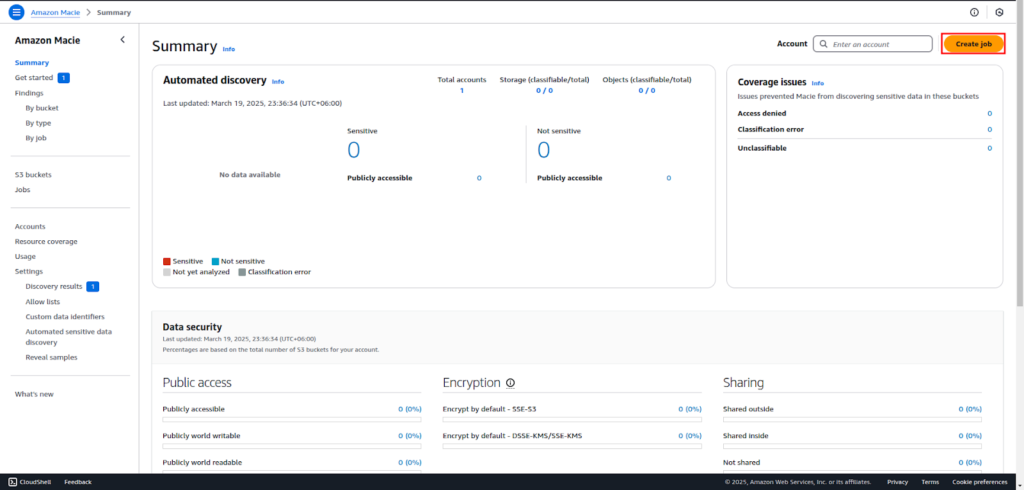
Select the S3 bucket that contains test_data.txt.
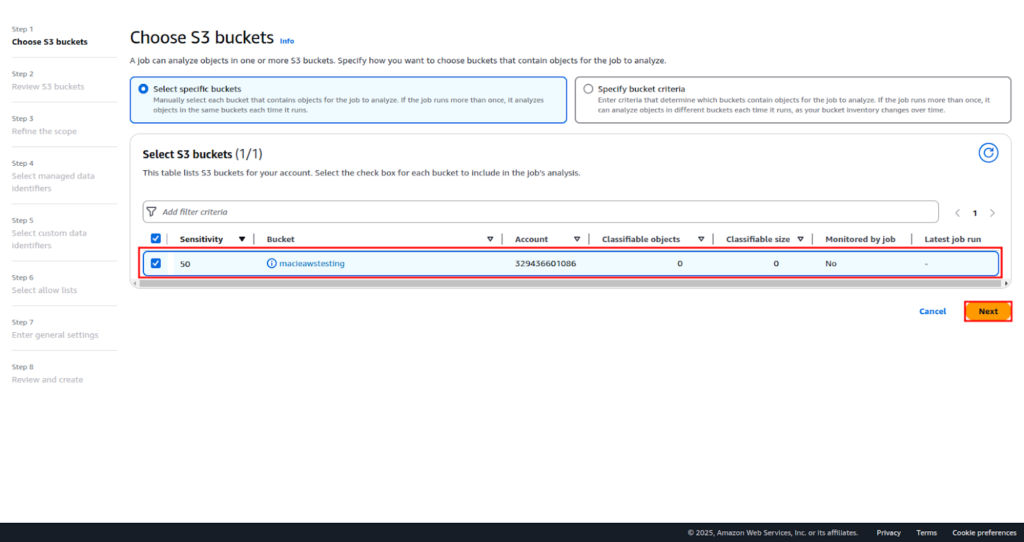
Click Next. Review the S3 buckets and click on Next again.
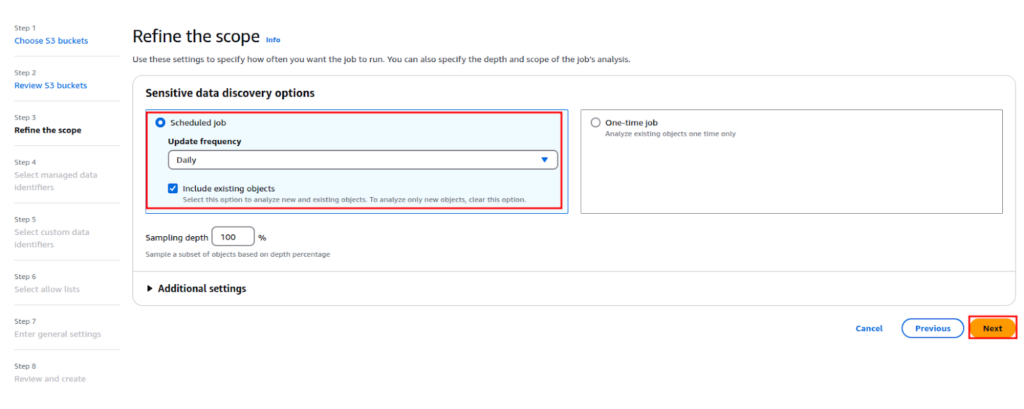
Here select how often you want your data to get scanned, and hit Next.
Now choose your custom data identifiers or select the recommended ones and click Next.
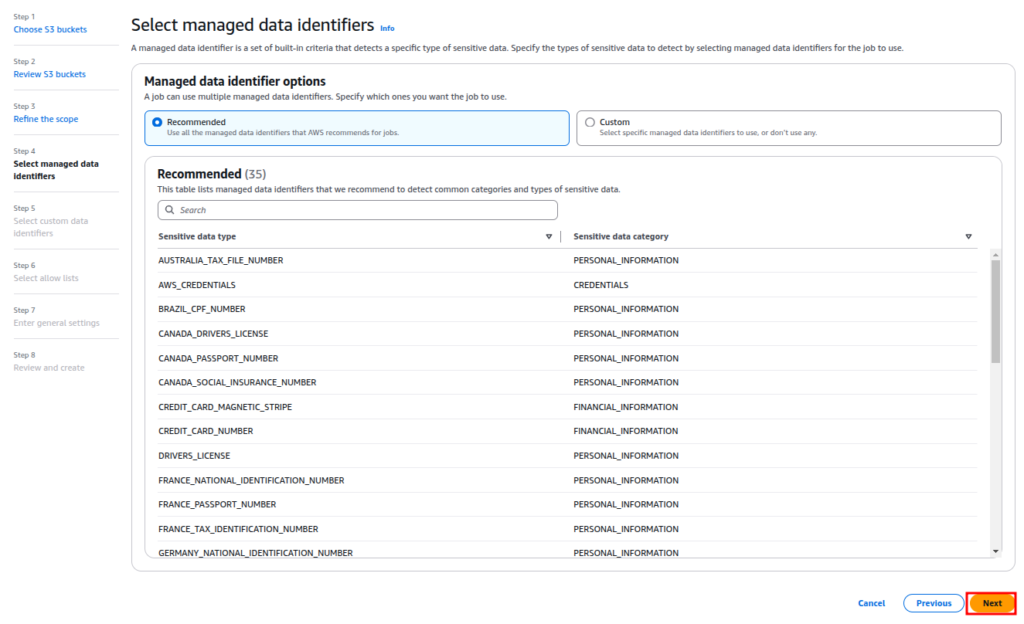
You can create custom data identifiers or allow lists if you would like to for this tutorial we’re going to skip these stages.
Enter a job name and description and proceed to the final section.
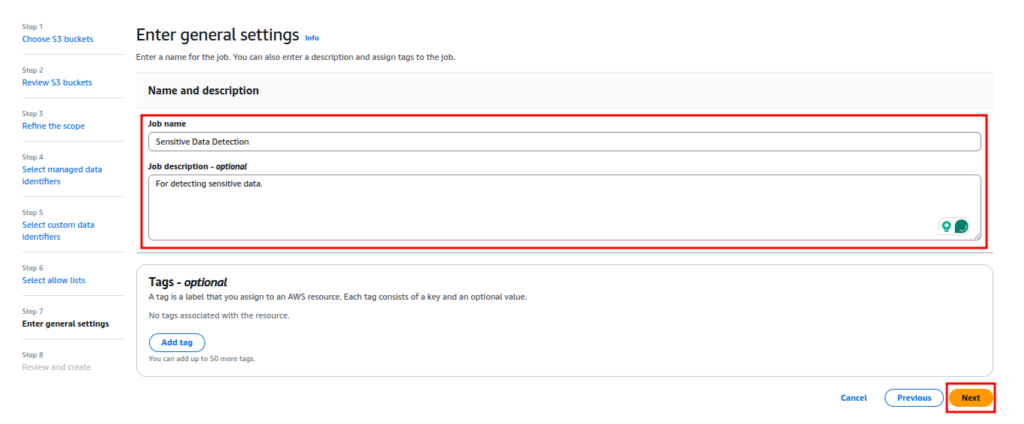
Now review all the units and click the Submit button to create the job.
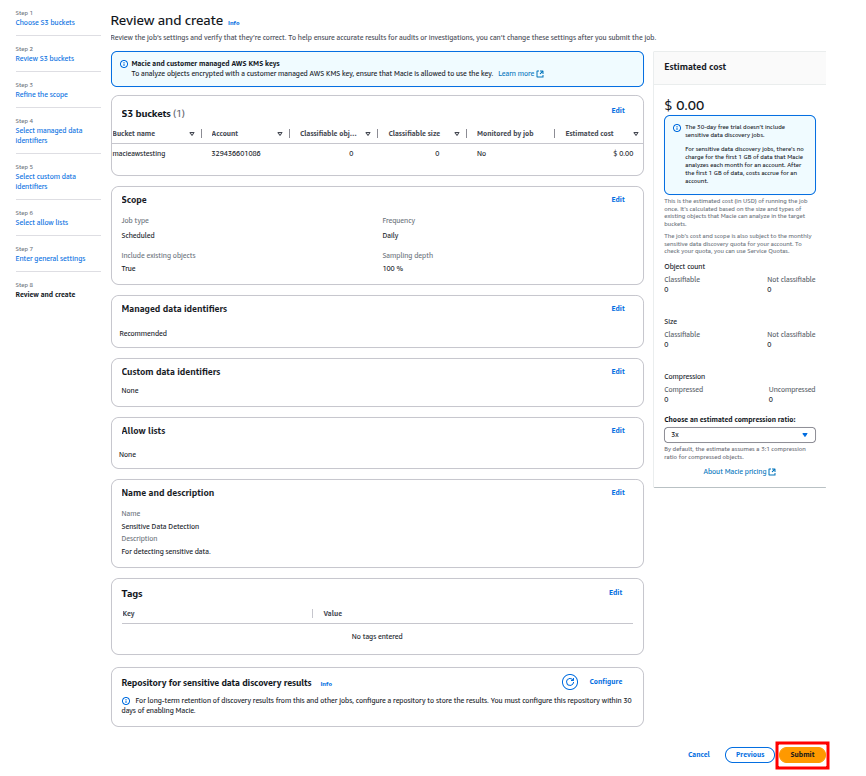
The scanning process will begin, and Macie will analyze the files in the S3 bucket.
Step 4: Review Macie’s Findings
Once the scan is complete, we can check if Macie identified the sensitive data in test_data.txt.
1. View Findings
In the AWS Console, go to Macie. Click on findings to see if Macie flagged test_data.txt.
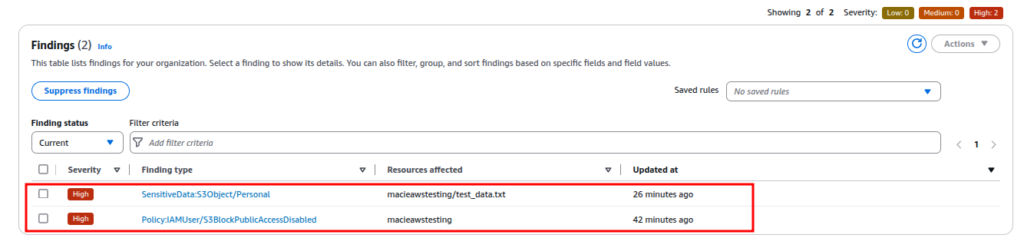
We can see Macie has detected 2 findings one for sensitive data and the other one for publicly accessible S3 Bucket.
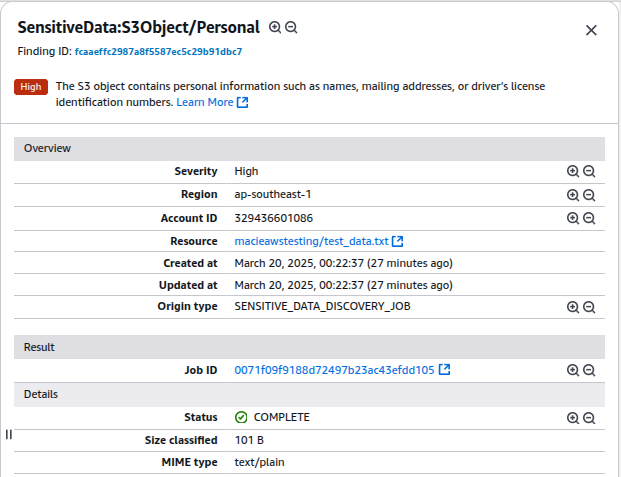
Click on a finding to see details:
Type of sensitive data detected (e.g., Credit Card Numbers, PII).
Severity Level (Low, Medium, High).
S3 Bucket Name where the file is stored.
Step 5: Remediate Security Issues
If Macie detects sensitive data in an unprotected S3 bucket, you can take the following actions:
1. Restrict S3 Bucket Access
Go to Amazon S3 then Select the affected bucket. Now click Permissions and disable Public Access.
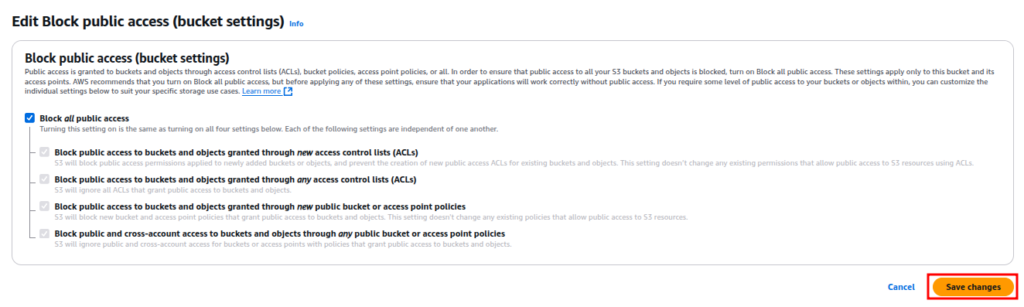
Then select Save Changes.
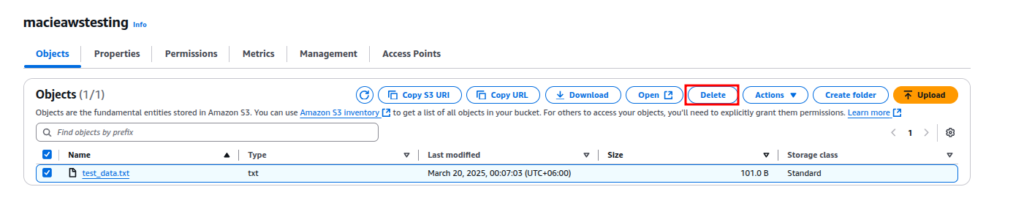
2. Delete the Sensitive File
If the file contains real sensitive data, delete it:
- In Amazon S3, go to the bucket.
- Locate test_data.txt.
- Click Delete.
AWS Macie
Running wide scans on S3 data can get expensive. Elite Cloud helps you scope Macie jobs intelligently. So you secure sensitive data without scanning the entire bucket unnecessarily.
Connect with us to optimize security monitoring and cost.
Conclusion
AWS Macie is a powerful tool that helps organizations protect sensitive data in the cloud by providing automated discovery, classification, and monitoring of data stored in Amazon S3. By leveraging machine learning and pattern matching, Macie can identify personally identifiable information (PII), financial records, and other confidential data, enabling security teams to take proactive measures against potential risks. As cloud environments grow, implementing tools like Macie becomes essential for maintaining visibility and control over sensitive information.
FAQs
What is AWS Macie used for?
AWS Macie helps identify and protect sensitive data like PII and credit card numbers in Amazon S3 buckets using machine learning and pattern recognition.
How does AWS Macie scan my data?
You create Macie jobs that scan selected S3 buckets for sensitive content. It checks for data types and access risks like public exposure.
Can I use AWS Macie with fake data for testing?
Yes, you can upload test files with mock PII or financial data to safely evaluate Macie’s detection capabilities in a controlled environment.
What happens after Macie finds sensitive data?
Macie generates findings showing the data type, severity, and file location. You can use this to restrict access or remove the data entirely.
Is AWS Macie only for S3?
Currently, Macie is focused on scanning Amazon S3, but it’s highly effective for managing compliance and securing cloud-stored data.




